In order to achieve this in POC we need to have Below prerequisites we need at least two VM's
1 Ansible Controler / Ansible Tower
OS: Redhat 9
IP : 192.168.1.11
2 Ldap Server
OS: redhat 9
IP : 192.168.1.17
On the ldap server there is podman installed by default if not install podman its a alternative to docker
launch a podman container with ldap with below command
# podman run -p 389:389 -p 636:636 --name my-openldap-container osixia/openldap:1.5.0 --env LDAP_ADMIN_PASSWORD="admin"
if you are not an expert with ldap and required GUI then launch another podman container
# podman run -p 443:443 --env PHPLDAPADMIN_LDAP_HOSTS=192.168.1.17 --detach osixia/phpldapadmin:0.9.0
Once you done with launching two containers you need to test that they are working/ in running state
[root@localhost ~]# podman ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
d560d0d2d420 docker.io/osixia/phpldapadmin:0.9.0 10 hours ago Up 10 hours 0.0.0.0:443->443/tcp suspicious_albattani
116f874f9da6 docker.io/osixia/openldap:1.5.0 10 hours ago Up 10 hours 0.0.0.0:389->389/tcp, 0.0.0.0:636->636/tcp my-openldap-container
[root@localhost ~]#
open a brower and hit https://192.168.1.17/phpldapadmin
in the username cn=admin,dc=example,dc=org and in password admin these are the default values for ldap server to login
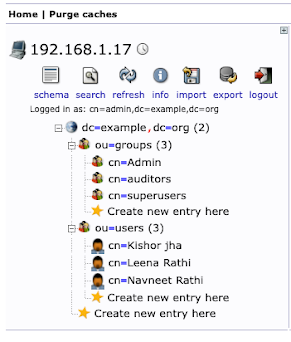
you need to create bunch of groups and users in the ldap to keep the things simple i have shared the export here
# LDIF Export for dc=example,dc=org
# Server: 192.168.1.17 (192.168.1.17)
# Search Scope: sub
# Search Filter: (objectClass=*)
# Total Entries: 9
#
# Generated by phpLDAPadmin (http://phpldapadmin.sourceforge.net) on March 7, 2024 11:09 pm
# Version: 1.2.5
version: 1
# Entry 1: dc=example,dc=org
dn: dc=example,dc=org
dc: example
o: Example Inc.
objectclass: top
objectclass: dcObject
objectclass: organization
# Entry 2: ou=groups,dc=example,dc=org
dn: ou=groups,dc=example,dc=org
objectclass: organizationalUnit
objectclass: top
ou: groups
# Entry 3: cn=Admin,ou=groups,dc=example,dc=org
dn: cn=Admin,ou=groups,dc=example,dc=org
cn: Admin
gidnumber: 500
objectclass: posixGroup
objectclass: top
# Entry 4: cn=auditors,ou=groups,dc=example,dc=org
dn: cn=auditors,ou=groups,dc=example,dc=org
cn: auditors
gidnumber: 502
objectclass: posixGroup
objectclass: top
# Entry 5: cn=superusers,ou=groups,dc=example,dc=org
dn: cn=superusers,ou=groups,dc=example,dc=org
cn: superusers
gidnumber: 501
memberuid: nrathi
objectclass: posixGroup
objectclass: top
# Entry 6: ou=users,dc=example,dc=org
dn: ou=users,dc=example,dc=org
objectclass: organizationalUnit
objectclass: top
ou: users
# Entry 7: cn=Kishor jha,ou=users,dc=example,dc=org
dn: cn=Kishor jha,ou=users,dc=example,dc=org
cn: Kishor jha
gidnumber: 500
givenname: Kishor
homedirectory: /home/users/kjha
objectclass: inetOrgPerson
objectclass: posixAccount
objectclass: top
sn: jha
uid: kjha
uidnumber: 1001
userpassword: {MD5}ISMvKXpXpadDiUoOSoAfww==
# Entry 8: cn=Leena Rathi,ou=users,dc=example,dc=org
dn: cn=Leena Rathi,ou=users,dc=example,dc=org
cn: Leena Rathi
gidnumber: 502
givenname: Leena
homedirectory: /home/users/lrathi
loginshell: /bin/bash
objectclass: inetOrgPerson
objectclass: posixAccount
objectclass: top
sn: Rathi
uid: lrathi
uidnumber: 1002
userpassword: {MD5}ISMvKXpXpadDiUoOSoAfww==
# Entry 9: cn=Navneet Rathi,ou=users,dc=example,dc=org
dn: cn=Navneet Rathi,ou=users,dc=example,dc=org
cn: Navneet Rathi
gidnumber: 500
givenname: Navneet
homedirectory: /home/users/nrathi
loginshell: /bin/bash
objectclass: inetOrgPerson
objectclass: posixAccount
objectclass: top
sn: Rathi
uid: nrathi
uidnumber: 1000
userpassword: {MD5}ISMvKXpXpadDiUoOSoAfww==I have created 5 groups
- groups
- users
- superusers
- Admin
- auditors
I have created 3 users
- Navneet Rathi --> nrathi (system Administrator) Memberof superusers group
- Kishor jha --> kjha (Normal user) Memberof Admin group
- Leena Rathi --> lrathi (Syste, Auditors) Memberof auditors group
Once done with this we need to look at the redhat Ansible aap /Ansible tower where we need to configure the RedHat aap /Ansible tower
ref : https://github.com/osixia/docker-phpLDAPadmin
ref : https://docs.ansible.com/automation-controller/latest/html/administration/ldap_auth.html



